Exercises
Note about TPA data and demo environments
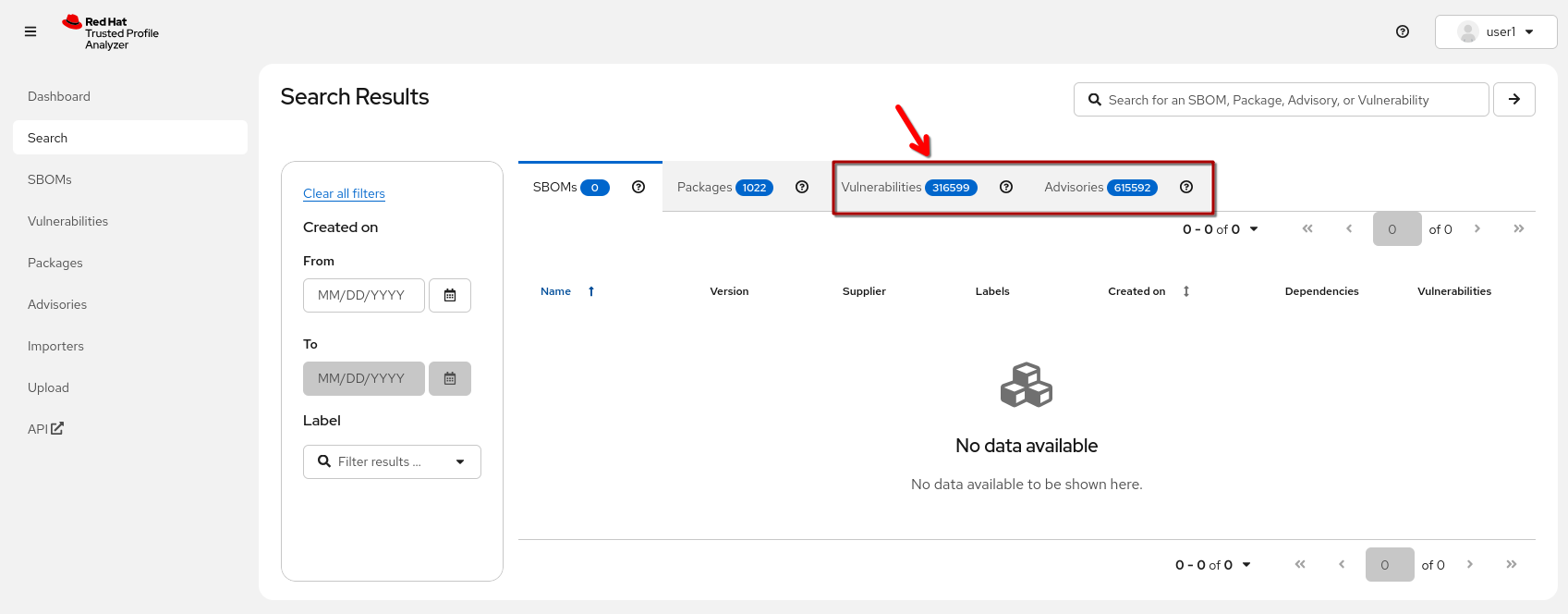
To make sure you have enough vulnerability data to actually match some vulnerabilities to your SBOMs, here are a few locations you can check: (Login with 1) The {tpa_url}/search[Search View^,window="tpa"] provides the numbers for currently ingested CVEs and Advisories 2) The {tpa_url}/importers[importers view^, window="tpa"] gives you the status of the last importer runs. You need to have a user with |
Prerequisite: Setup TPA Manager user
The TPA default setup (inherited from the ADS demo for consistency) comes with a user1 with read-only access level and an admin.
This is completely fine or a demo, highlighting the typical use cases. For some of our exercises later, we need a user with some more access - and we have a script that will create one.
|
You can use the same scripts with the ADS demo, should the need arise - feel free to check them out and re-use as you like. |
To quickly configure our tpa-manager user, first open a {openshift_console_url}/terminal[terminal^,window="terminal"].
If asked, login as {openshift_admin_user} with {openshift_admin_password}
|
If you have done previous modules, you’re probably aware of shared user sessions between the admin console and other Lab content. In our setup, TPA uses a different realm ("Trusted Content") so there is no problem here. For the following exercises, it doesn’t matter which one you’re using. |
In our terminal, clone the "helpers" repository (if you already have, go to the ``)
cd #to start from "home"
git clone https://github.com/redhat-tssc-tmm/l3-enablement-helpers.git
cd l3-enablement-helpers/tpa-tssc
./create-tpa-manager.shWe have created a user tpa-manager with password r3dh8t1! that we can use for exercises that require more than read:document access.